Now you can Hack e-mails!

|
Hack Emails
Hack Emails
Hacking is a well-known activity among Internet users, however, it can be a complicated process. 🕵️
In this space we will not only give you the processes that you can test to hack, you will also be able to enter an Email account without being detected.
How to Hack Email Step by Step
The world of online hacking is growing exponentially, offering attractive alternatives that do not require prior knowledge. Thanks to these new innovations, obtaining the data required to hack an Email is very simple and, best of all, very fast.
Free platforms like Account.st they can offer you in just minutes the exact data to enter any email account you want. The most attractive thing about this method is that you can use it remotely and completely anonymously.
Steps:
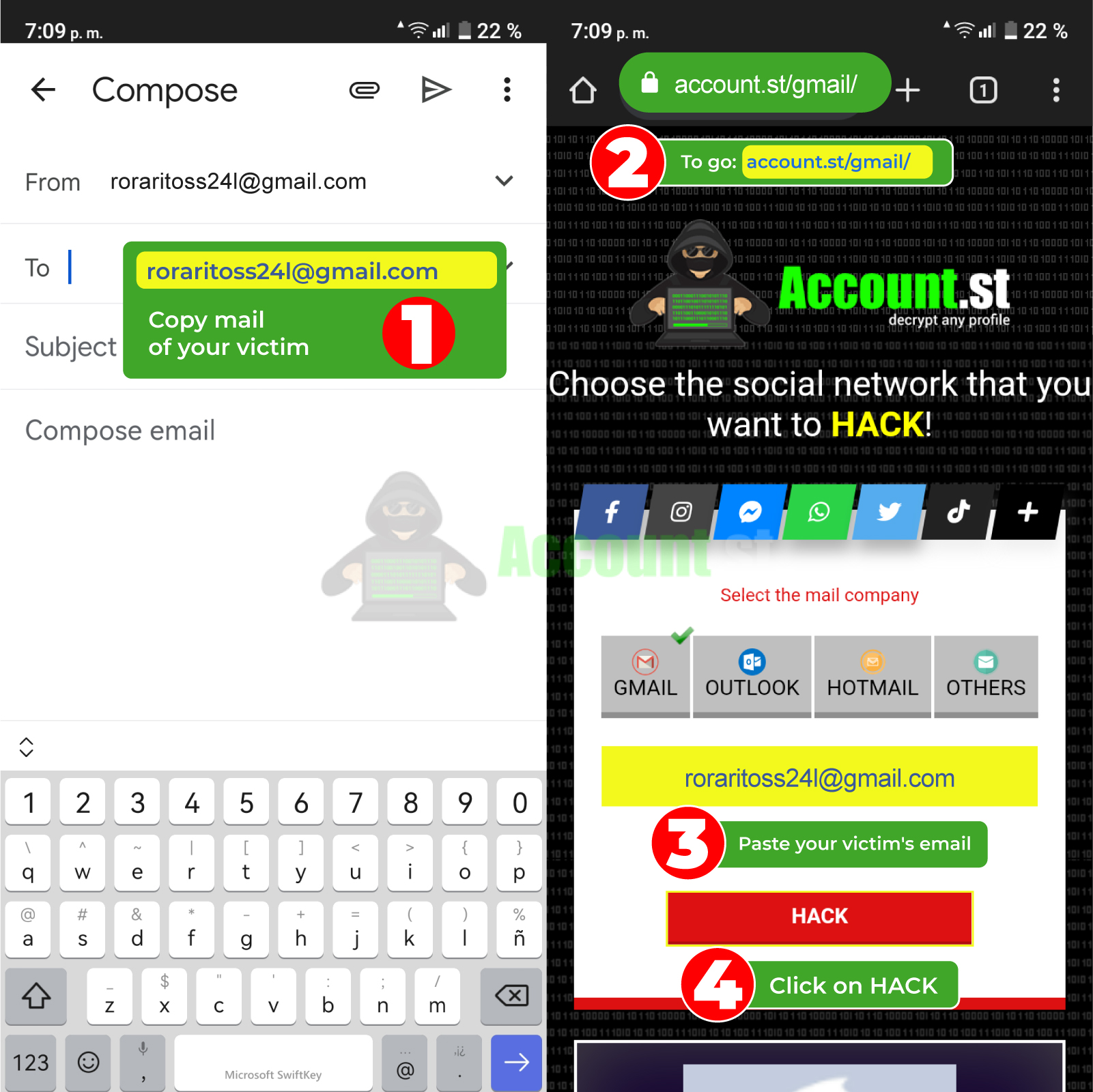
- You just need to copy your victim's email address
- Then go to the page https://account.st/email/
- Paste it in the search bar.
- Then press "Hack".
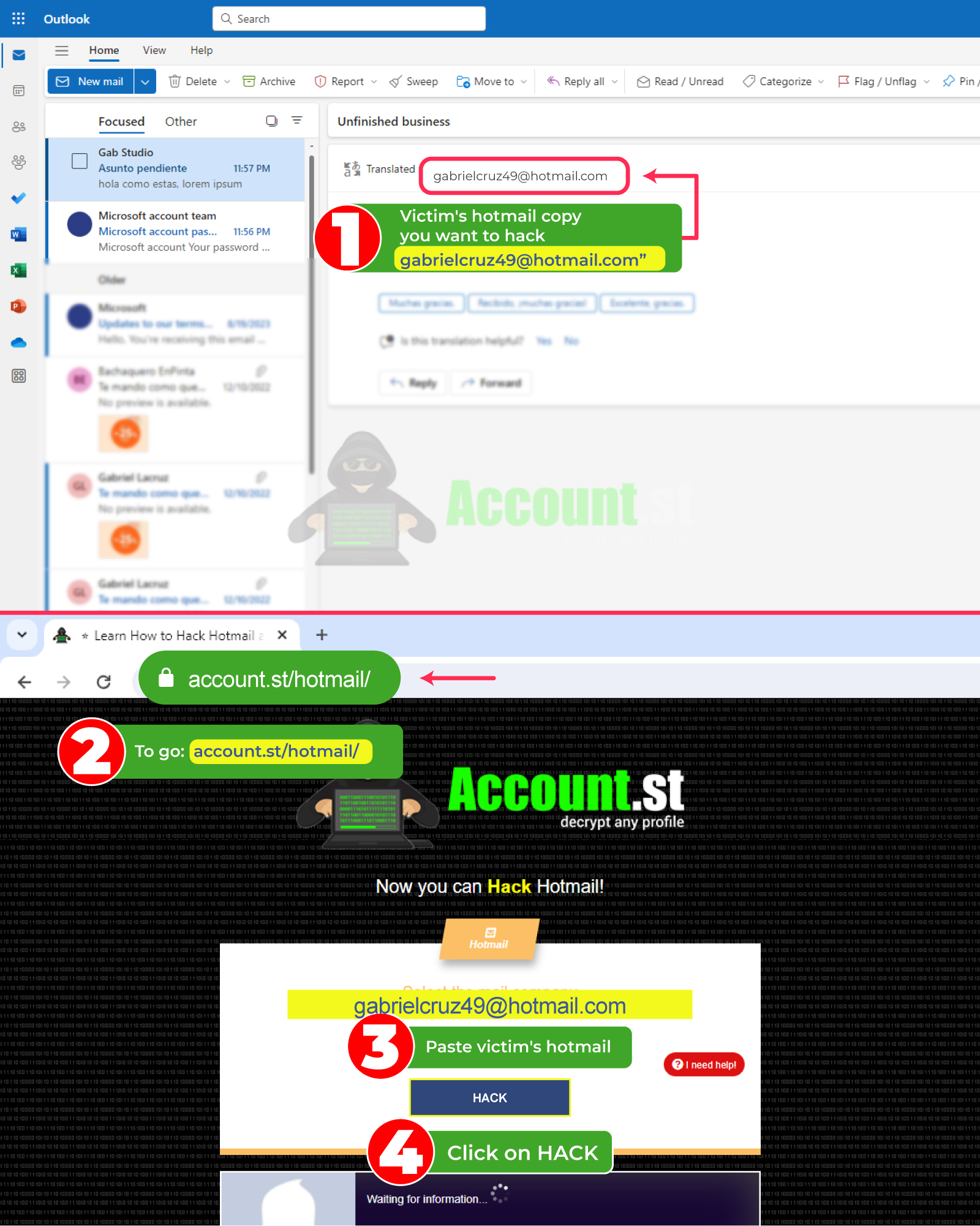
In a few minutes the system will provide the necessary credentials, so you can copy them and access the Email account of any person you want. Under this modality, enter a very simple Email account, but above all effective.
2024 Methods to Hack Email
This 2024, hacking techniques will be available to anyone who wants them and for greater benefit, many are easy to use. You can also apply them for free and those that are paid have really affordable costs.
Take a look at all the techniques and innovative technology to hack an Email account in a few minutes and without having prior experience.
Hack Email with Login-online.me
Logins are mostly free tools that simulate the login of almost any platform. Thanks to its increasing updating, there are more and more platforms that it can copy, which allows the deception to not be noticed, not even by the most detailed eye.
Its main function is to obtain the exact data of anyone who innocently enters the malicious link. Its greatest attraction is that it can perfectly simulate social media platforms, credible banking entities, and much more.
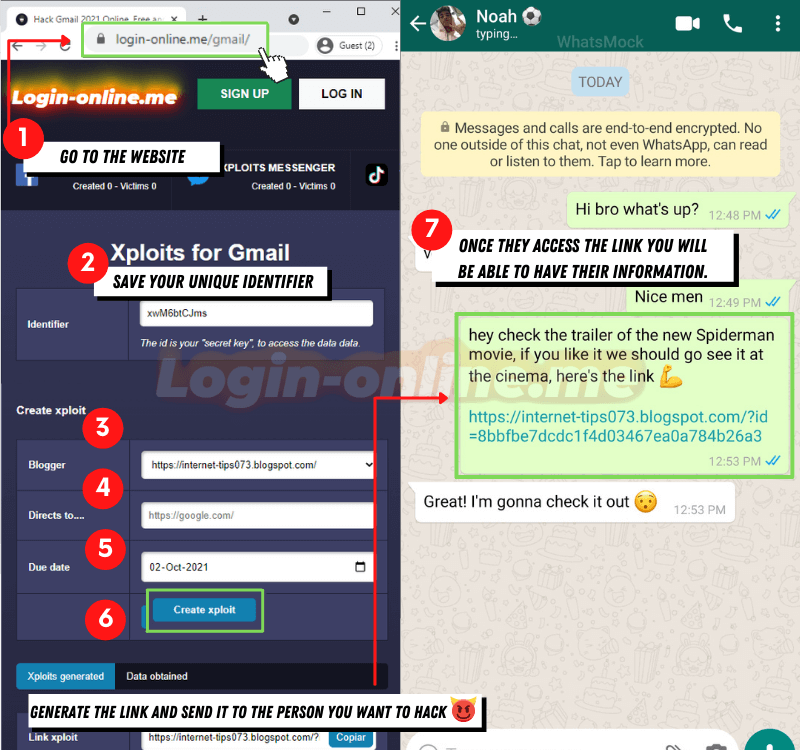
Logins are very versatile when it comes to creating effective methods to deceive a third party and obtain their data effectively and anonymously. Therefore, the victim almost never sees the difference between the official platform and the Login.
- Its method of use is very simple, although the “Login” is very well prepared, the process is not at all difficult to carry out. First enter the page https://login-online.me/ and select the platform or entity you want to imitate, to create the Login.
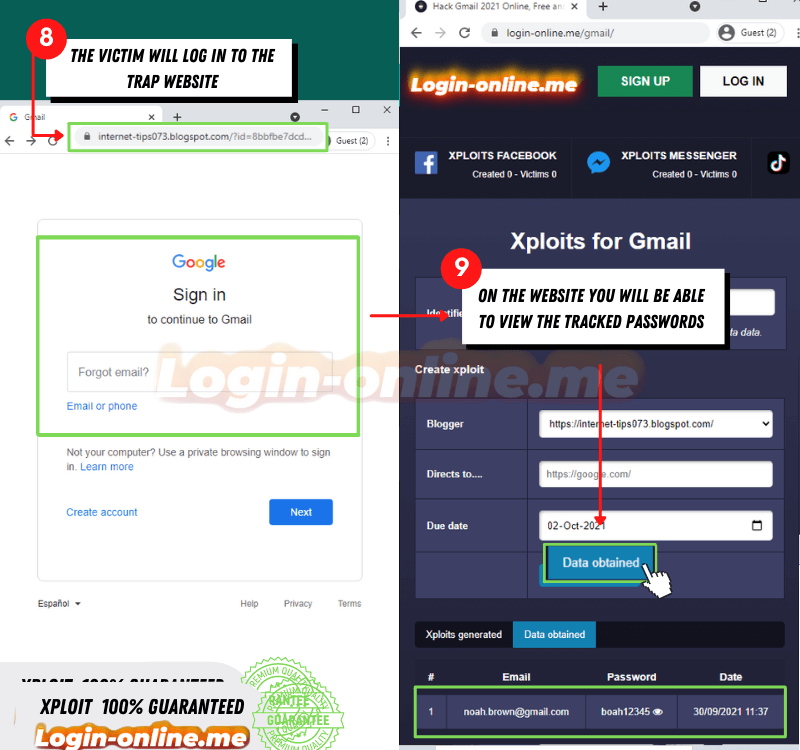
Once you select it, you must proceed to follow the steps to create the Scam. This will allow you to simulate the login of the platform you want, and in this segment, you must choose the expiration date of the scam and its design.
Once you have finished all the steps, press the create option and wait a few minutes while the page is created. When it is created, copy the URL or link and proceed to send it to the person you want to hack.
It is important that when sending the link, it is accompanied by a message to add greater trust to the third party. In this way, the victim will trust and voluntarily provide their data in the login created later.
To access the credentials, go to the platform and enter the credential option. This way you can collect the data and enter your Email account in minutes.
Hack Email with FraudGPT
Artificial intelligences are increasingly involved in all types of technological activities, allowing us to minimize large workloads. Of course, they have also been in charge of creating intelligent tools, capable of violating anything on the network remotely.
FraudGPT is an artificial intelligence with the ability to enter remotely and anonymously to any platform located on the web. Created from the base of ChatGPT, this AI has everything necessary to breach and even offer effective hacking solutions and options.
What makes FraudGPT different from ChatGPT? FraudGPT has no limitations or filters, so hacking is not penalized and is allowed within this AI. From here you can request methods, apps, tools and more to hack any platform, including Email accounts.
Another difference is that ChatGPT is an app that you can use for free, while FraudGPT you must pay for it and you can only locate it on the dark web, since its use is for mostly illicit activities.
Hack Email with saved browser passwords
An everyday tool in our browser that can be used to access social media accounts, and more is the password manager. This segment houses not only logins, but also accurate and confidential information, such as passwords, users, and more.
In order to access this information, it is essential that you have access to the third party's computer or mobile device. This way you can enter your browser and view, from settings, your automatically stored passwords and logins.
🌐 In order to locate the passwords and enter the Email account you want, you just have to follow these instructions:
- From your victim's device or computer, enter the browser.
- Go to the configuration box and locate https://passwords.google.com/ or password manager.
- Once located, press enter and locate the password and users for the Email account in the list of options.
- To finish, copy them and then enter your email account from the official platform.
Hack Email from Wi-Fi browsing log
Violating an Email account from a Wi-Fi network is possible and we will tell you how to take advantage of the registration data of your victim's Wi-Fi network. To carry it out you need to follow the steps that we will detail below.
- Find the IP address of your router.
- Press Windows + R to open the Run window.
- Type cmd and press Enter.
- In the command prompt window, type ipconfig and press Enter.
- Find the line that begins with Default Gateway. The IP address that appears next to it is that of your router.
- Look for the browsing log: this may vary depending on the model and brand of your router.
- Look in the router settings for a section called Security, Logs, or Advanced.
- When you find the option, you will be able to see the browsing log and a list of websites visited from devices connected to the Wi-Fi network.
Spy Email from browser history
Browser history is a tool used to keep track of everything we do on the web. This houses which pages we visit from, which platform we frequent the most, logins and much more.
So, if you manage to access your victim's device, getting to their data will be very easy to do. The only thing you have to do is enter your browser from your mobile or computer, then in the upper right part of the screen select the configuration box.
Once there, scroll down and look for the history option and click on it, then all of your victim's activity will appear. Locate the app or Email account you want to hack and copy its stored data.
Spy on Google activity
Another option, if you want to take advantage of the browser, is to search for Google activity, where user credentials are stored in a more organized way. So, you will be able to see the access information of the Email account and any social network in more detail.
💪🏼 To access you just have to follow this procedure:
- From your victim's mobile or laptop, enter https://myactivity.google.com/
- Upon entering, you will be able to view a list of your recent activity.
- If initially you cannot locate the email account, you can filter by date and name, this way you will be able to locate it much faster.
- Once you locate the account, log in and you will be able to see all the access information you need.
Spy Email with find my device
Google's security tools, in case your devices are lost or stolen, also contain valuable information to hack Email accounts. You just need to enter your victim's Google browser and look for the option to Find your mobile and copy your victim's data.
This way you can spy on their web activity, logins and much more in real time.
Spy Email with Google Location
If what you want is to know from which location your victim is connecting in real time, this tool will help you. The best thing is that the process is simple, although it is important that you have access to a device to be able to access your browser.
- Open Google Maps in your web browser: https://www.google.com/maps/timeline
- Make sure you are signed in to your Google account.
- Click the menu (three horizontal lines) in the upper left corner.
- Select - chronology-
🕵️ Once you access your Chronology you will be able to view:
- Summary of the places you have visited on a map.
- You can filter by date to see your history on a specific day.
- You can turn Location History on or off to control whether Google saves your location over time.
What other ways are there to hack?
You have seen many of the modalities for hacking, with systems that we use on a daily basis. If you have greater knowledge and want to obtain much more reliable results, these methods will undoubtedly provide everything you need.
Hack Email with Cookies
Cookies are tools that store a large amount of information about people on the web. These are responsible for storing our preferences on the Internet. In addition to hosting confidential information and data of great value.
Accessing the cookies on the device, social networks or systems allows you to obtain the data you want from the third party. Which will undoubtedly help you access not only your Email account, but all your accounts and devices.
Hack Email with Artificial Intelligence
AIs are increasingly moldable and modifiable by expert hackers, to provide infallible hacking knowledge.
Just by entering the deep internet you can find artificial intelligence programs that are proof of anything, without filters and safely. Of course, you will have to buy it, since being such an effective tool it has a one-time cost of use.
Hack Email with Malware
Malware, like viruses, are programs and tools that work in the background without being detected. Thanks to their great ability to camouflage and simulate being part of any technological system they enter, they can operate remotely without being detected.
Its main function is to corrupt systems, modify, damage, extort or steal confidential information from a third party, without them noticing in most cases.
Hack Email with Windows Command Prompt
Windows command prompts are advanced commands that allow you to modify platform codes, websites, and social networks at will. This in order to steal, infiltrate and detect security breaches. It is essential to have prior knowledge to apply this method, since it requires certain programming skills.
Hack Email with Trojan
Trojans are another hacking method widely used by hackers. This is due to its great ability to simulate websites, social networks, email accounts or banking entities and more accurately.
Its function is to deceive the third party, posing as trustworthy entities and platforms, gaining the trust of the victim.
Hack Email with Virus
Viruses are one of the most used methods when hacking, as they are infallible and easy to learn to use. They top the lists of popular hacking methods on the web and the margin for error is almost zero.
There are two ways to use viruses: one for data theft, which refers to interfering with systems with weak security. Which allows the hacker to collect valuable data that allows entry to all the victim's networks, platforms and devices.
The second way is to infiltrate the devices and cause irreversible damage to them. They also often disable to persuade the victim to provide the data they need to hack.
Hack Email with Spyware
Spyware is the most sought after and downloaded program by many users, thanks to its wide range of hacking abilities. In addition to being a remote tool with functions that will undoubtedly be very useful.
This stands out for collecting all the information you type on your devices, in addition to having access to the cameras. You can access device location, history and much more.
Hack Email with Adware
Adware on its own is usually harmless, but many of them can hide viruses or malware that hinder the user experience on any network. Even managing to steal valuable data and permanently damage devices.
Adware is an advertising banner that can be annoying, removing spaces or popping up at the wrong time. But they are also used to steal data when you click on them, which makes them effective when it comes to compromising social media accounts or emails.
Hack Email with Ransomware
A method that is responsible for collecting information, almost impossible to obtain, is Ransomware. These are responsible for stealing encrypted information from almost any social network, including email accounts.
Using encrypted information, Ransomware can interfere with or intercept images, emails, user passwords and valuable personal information. Which allows the hacker to manipulate the victim financially, so that they pay to recover their data.
Hack Email with SQL Injection
SQL are malicious commands that, through the injection method, infiltrate any platform or system, allowing vulnerabilities to be detected. These vulnerabilities can be weak passwords, few active security commands, and public sensitive information.
Through SQL injection, hackers can enter Email databases or any platform and steal information necessary to enter. All remotely and anonymously.
Hack Email with DNS Poisoning
DNS poisoning is a third-party redirection method to a malicious platform. This platform usually has the design of official platforms on the web, so the third party cannot notice the deception.
In this way, the hacker manages to manipulate the DNS by sending the victim to another website, thus allowing the login data of their Email accounts and any network they wish to be stolen.
Hack Email with Spoofing
Spoofing is a hacking method that depends on the persuasion power of the person who executes it. Of course, also supported by other methods, such as hacking devices using Google location.
This method is based on impersonating technical support or network assistance personnel or the platform you want to access. To make the deception more effective, the hacker can activate the device's mechanisms using Google's location.
In this way, the third party agrees to provide the data requested by the hacker, allowing their systems to be completely and effectively violated.
Hack Email with Hijacking
Hijacking is another infiltration method that is characterized by the complete takeover of a third party's systems and platform. This is responsible for studying the platform you want to hack, locating the system's weaknesses and exploiting its vulnerabilities until you can hack.
This method can take a few minutes or days, depending on the system and the skill of the person using it. But its effectiveness is 100%, allowing remote and anonymous access to any system and having absolute control of it.
How to protect your Email account?
- 🔐 Know the methods of web hacking to take proper precautions.
- 🔐 Keep your devices updated to ensure the security of your digital platforms.
- 🔐 Always verify logins from the official platform to avoid phishing attacks.
- 🔐 Avoid opening unsafe links, even if they come from known contacts.
- 🔐 Pay attention to advertising banners and suspicious activity on your devices to avoid credential interception.










