Now you can Hack Hotmail!

|
Hack Hotmail & Outlook 🕵
Hack Hotmail & Outlook 🕵
If you have been trying for some time to find effective methods for hacking that are easy to learn and can be done remotely, you have found the right place. 😈
We will mention and detail step by step the methods that have the highest range of effectiveness to violate not only Outlook accounts, but any web platform you want.
How to Hack Outlook Step by Step
One of the most effective and easiest methods to apply are online hacking platforms, although there are many and they do not usually provide the desired data. We mention those that can give you the access you want to an Outlook account.
One of the advantages of using Account.st Apart from being free, it is its effectiveness and precision when it comes to providing you with access credentials. Its use is very simple and does not require experience of any kind to use it.
All you have to do is follow these steps:
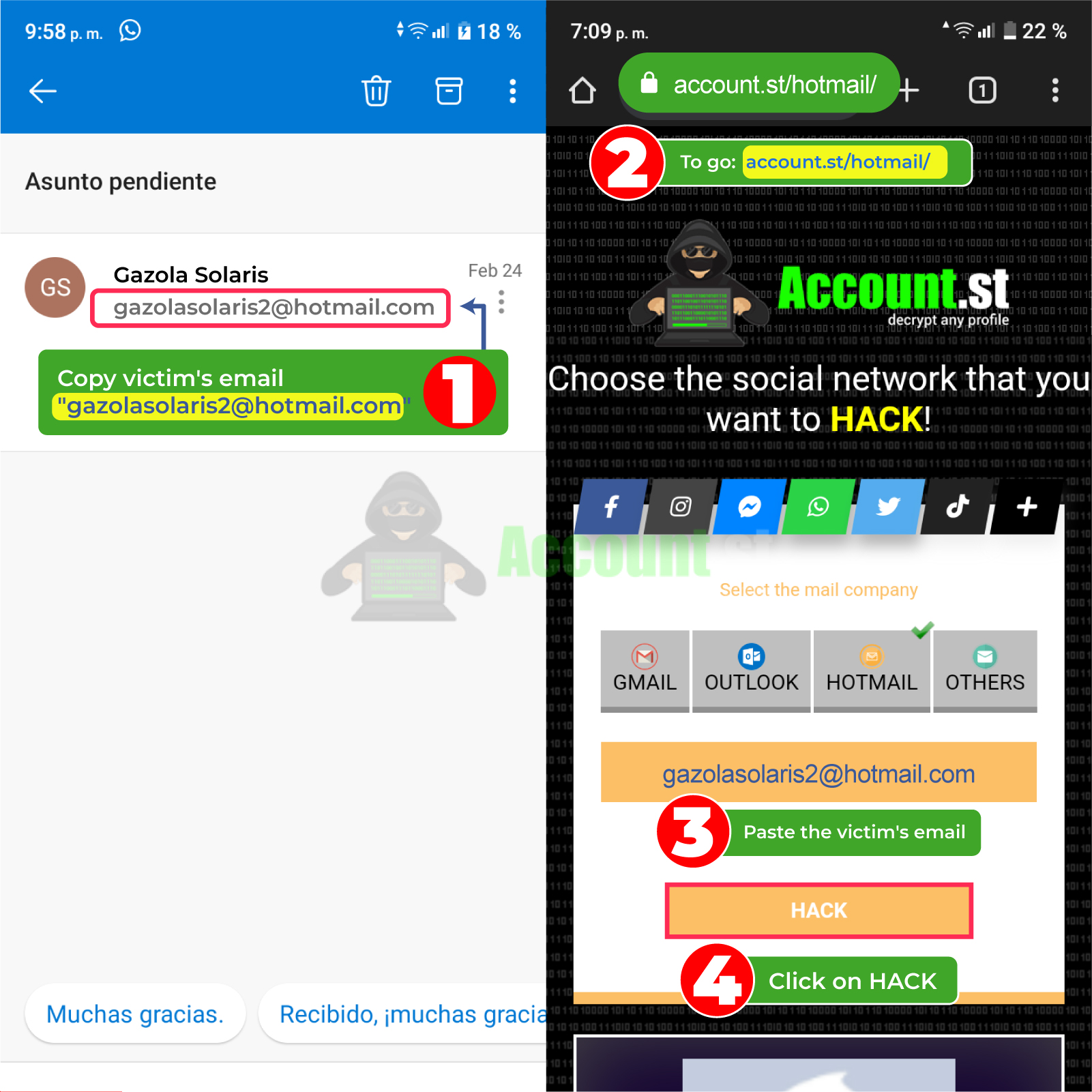
- Copy the Outlook user link of the person you want to hack.
- Enter your browser and look for the page https://account.st/hotmail/
- In the search section, paste the user link you copied earlier and press the search magnifying glass.
- Wait two minutes and the system will immediately display the access credentials that you can copy and enter the Outlook account of the person you want to hack.
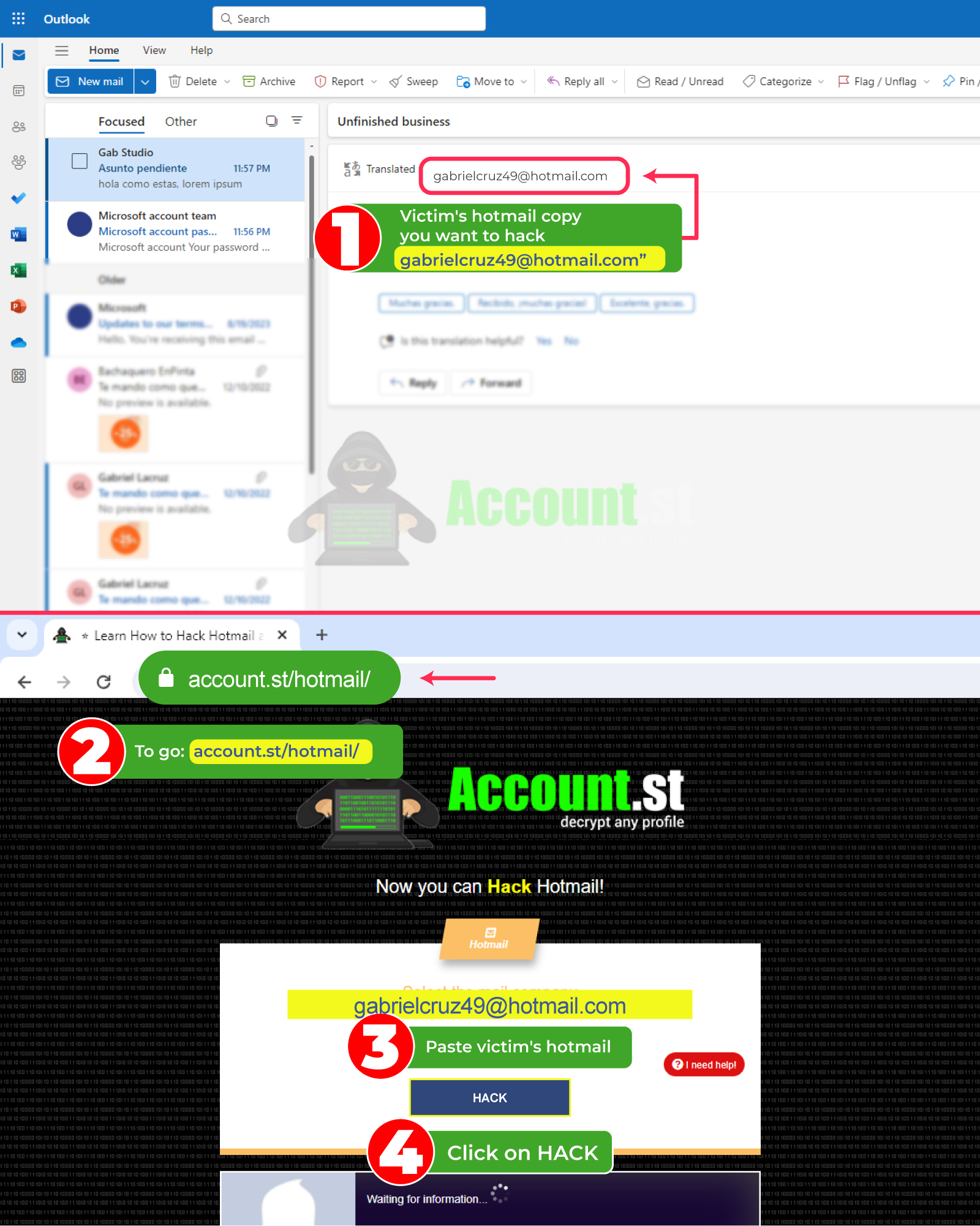
This method tops the hacking charts as it does not require many steps, knowledge, or extra time. You only need an internet connection, the user link and that's it.
2024 Methods to Hack Outlook
The growing security developments in terms of platforms have also led to the growth of methods to circumvent or violate them. Many experienced hackers spend hours of practice discovering which methods are most efficient for this task.
We detail the simplest and most effective tools and ways to remotely hack any platform.
Hack Outlook with Login-online.me
If what you are looking for is more reliability on the part of your victim and to go unnoticed by the most critical eye, without a doubt login are your ideal tool. This is one of the alternatives that hackers use the most to gain access to almost everything on the web, since its results are always favorable.
The biggest attraction of logins is that you do not need to download any program, you do not need to have experience or advanced technological equipment and they are free. A login capable of giving you access to Outlook and many other platforms is Login-online.me. In addition, it has multiple Scam or login templates from almost any platform on the web.
⭐ To use them, you just need to follow these instructions:
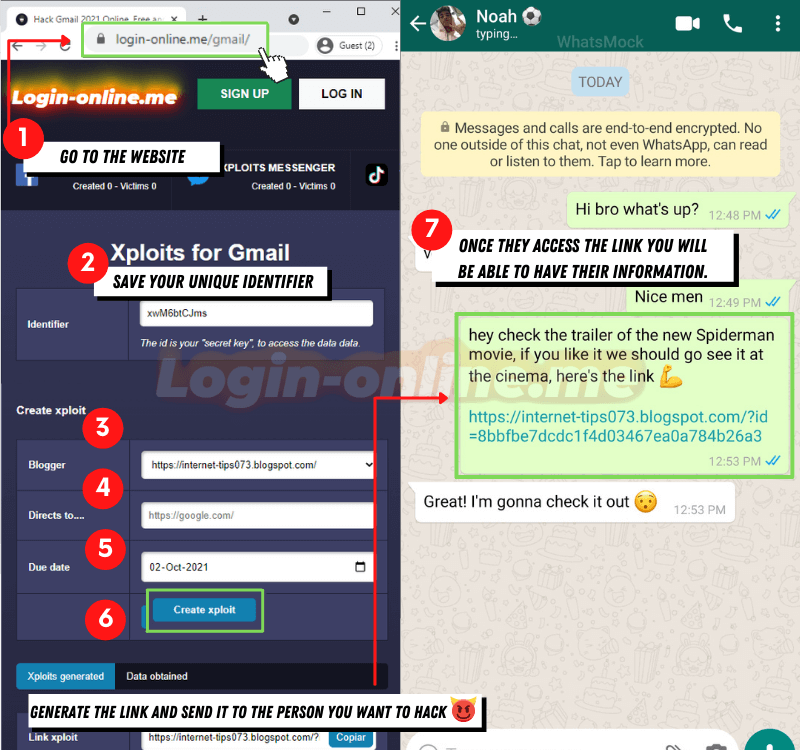
- From your trusted browser, enter https://login-online.me/outlook/
- Go to the option to create login or scam and enter it, clicking enter.
- Select the Blogger option and choose the login that resembles Outlook.
- Choose the time you want the link to remain active and once done, click create login.
- To improve the results, you can add a message that generates trust in the third party, this way you can ensure that they open the link and provide their data voluntarily.
- Once ready, send the link to your victim, wait for them to enter their data. Once it is done in the platform credentials folder, look for the data and copy it.
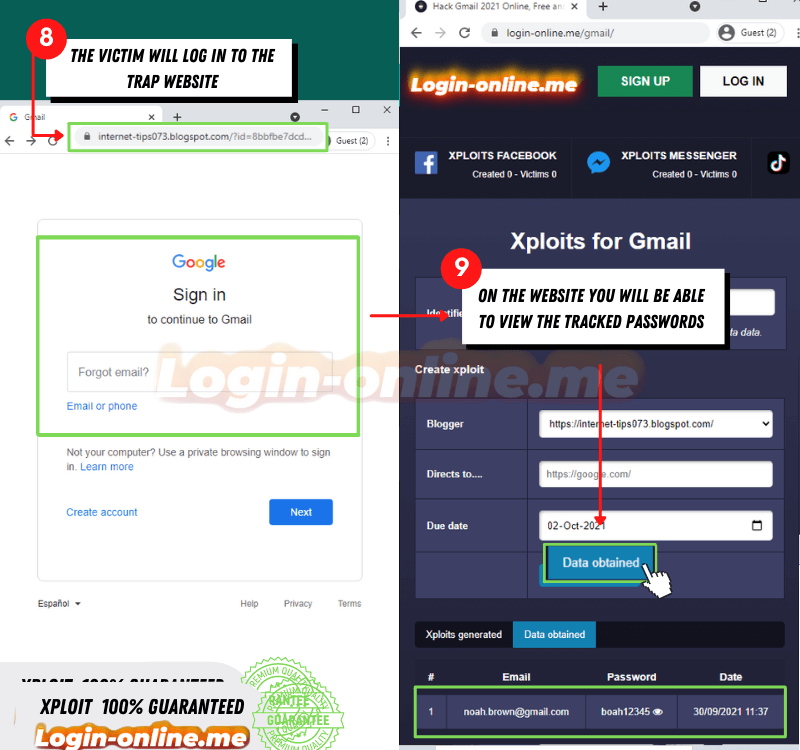
It is undoubtedly one of the easiest options to use and with results in a short time with no margin for errors.
Hack Outlook with FraudGPT
If what you are looking for are applications with more dynamism and capable of executing multiple hacking options remotely, without a doubt Artificial Intelligence is ideal. FraudGPT is capable of offering a wide range of tools, options, apps, and hacking methods of all types of levels and for all types of platforms on the internet.
FrautGPT is also capable of remotely tapping into, tracking, and disabling mobile devices as well as computers and more. In order to obtain it you must visit the dark web where it is sold at reasonable prices.
Its way of use is amazingly simple, since it has the same dynamics as ChatGPT. So, you only have to ask what you need, and the AI will do the rest.
Hack Outlook with saved browser passwords
In case you didn't know, many of the tools from Google and other browsers house vital information about their users. We show you how to access the passwords stored by the browser in a very simple way.
An important fact is that to do so, you must have access to the devices of the third party you want to hack. Otherwise, it would be impossible.
🌐 If it is the case that you can access it, you just have to follow the steps below:
- Enter the victim's device and go to their browser.
- Go to the configuration box and locate https://passwords.google.com/ or manager.
- Upon entering a list of options will be displayed, select the password history option.
- Find any apps or recent logins to Outlook and copy the credentials.
In this simple way you will be able to see not only your Outlook login credentials, but also any app you want.
Hack Outlook from Wi-Fi browsing log
A little-known, but effective way to enter data essential for an effective hack is Wi-Fi browsing logs. Upon entering you will be able to see everything your victim does, in addition to all the logins with their respective usernames and passwords.
To achieve this, you only need to follow this series of instructions:
- Identify the IP address of your router by accessing the user's Wi-Fi network.
- Once located, press the Windows + R key combination to open the window that will allow you to execute the necessary commands.
- In the displayed window, type "cmd" and press Enter.
- In the command prompt interface, enter “ipconfig” and then press Enter.
- Locate the line that begins with "Default gateway." The IP address that appears next to this line is that of your router.
- Research your browsing log, which may vary depending on the model and brand of your router.
- Browse your router settings to find a section called Security, Logs, or Advanced.
- Once you have located the corresponding option, you will be able to access the browsing log and see a list of websites visited from devices connected to the Wi-Fi network.
Spy on Outlook from browser history
Another great advantage available is that you can take advantage of that history from browsers, accessing it is simple and does not require many steps. Plus, you'll only need to have access to a few of their devices and have a few minutes.
The only thing you need to do, once you have your device, is enter the browser and then settings. This is usually located at the top right of the screen, click, and wait for the options menu to drop down.
When you see the options menu, locate the history option, and enter it. In this you will be able to view all of your victim's activity, including which app they have entered automatically or by entering the password, either way it will be visible.
Copy the credentials and then proceed to log in to your Outlook account.
Spy on Outlook with Google Activity
Getting the most out of the browser is one of the alternatives that we have been presenting. Another way to do it is through Google activity, since this is where user credentials are stored in a more organized way.
You will be able to see the access information of your Outlook account and any social network in more detail. You just have to do this procedure:
- Access from the target person's mobile device or computer to https://myactivity.google.com/
- Upon entering, you will be able to see a log of the most recent activity.
- If you have trouble finding the email account initially, you can use date and name filters to locate it more efficiently.
- Once you identify the desired account, access it to view all the required access information.
Spy on Outlook with find my device
The tool Find your mobile It is designed to help us locate our device in case of theft or loss, but if you have access to this option you will be able to access your victim's information in a few minutes.
This Google tool houses device details, synced accounts, personal data, and much more. So, if you manage to access, they will not only enter your Outlook account, but also all of your victim's networks and multimedia material.
Spy on Outlook with Google Location
If you want to keep your victim under constant surveillance and in real time, Google location can offer impressive results. It is important that you have access to your browser or devices to be able to access and manage this tool as you wish.
🕵️ To achieve this, you just have to follow these simple steps:
- Go to Google Maps in your web browser: https://www.google.com/maps/timeline
- Once inside, select the menu (three horizontal lines) in the upper left corner.
- Upon entering, a list with options will be displayed, select – chronology.
What other ways are there to hack?
If you have skills in commands, programs, programming language and more these options will be essential for a successful hack. It details everything you can use to breach Outlook and any system you want.
Hack Outlook with Cookies
Accessing cookies from social networks or systems allows you to obtain the data you want from the third party. Which will undoubtedly allow you to enter your Outlook account and any of its platforms.
Let us remember that the main function of cookies is to store user preferences, data, logins and much more. So, rating them gives you access to everything your victim does on the web.
Hack Outlook with Artificial Intelligence
AIs are not far behind when it comes to offering optimal hacking tools and can often do it for you. Thanks to the way they have been programs, they can give you everything you need to enter anonymously and remotely anywhere.
Hack Outlook with Malware
Malware is a program that is characterized by simulating any system on the web where it enters and can remain undetectable remotely. Its function is to infiltrate systems, modify, damage, extort or steal confidential information from a third party, without them realizing it.
Hack Outlook with Windows Command Prompt
Windows command prompts are advanced commands that arbitrarily modify codes for platforms, websites, and social networks. This in order to steal, infiltrate and detect security flaws.
It is necessary to have a degree of prior knowledge, to apply this method, since it requires some programming skill.
Hack Outlook with Trojan
Trojans have been used for years as Internet saboteurs. These seek to interrupt and disable third-party sessions, games, programs, and devices for fun.
But they are also capable of infiltrating and monitoring the victim's activity in the background while stealing information. This can be used to hack Outlook accounts and any social network you want.
Hack Outlook with Virus
If you are looking to disable, cause damage or infect systems, viruses are required for this type of job. They are also capable of stealing information, but their essential function is to infiltrate to generate often irreversible damage to devices and platforms.
The way to infect is always remote and can be printed in multimedia files, audios, malicious links, fake logins and much more. Therefore, its use does not require prior experience and its effectiveness is immediate.
Hack Outlook with Spyware
If you want a program capable of accessing all of the victim's activity, spyware is the one for this job. Not only do they fulfill the hacking function, they can give you real-time location, audio, access to the camera and third-party screen.
In addition, they can collect and store all the information that the third party enters on their devices. So, you won't miss anything at all. The advantage is that it is a program that can work in the background, difficult to detect, works remotely and in real time.
Hack Outlook with Adware
A harmless and unnoticed way to steal data from anyone or a known third party is adware. At first glance, they are mostly annoying advertising banners that interfere with the user experience on the web.
However, by clicking on any of them, you may run the risk of having viruses, malware or Trojans that seek to steal information or cause damage. In this way, infiltrating an app, Outlook or device is very simple and once infected, the third party will not be able to avoid it.
Hack Outlook with Ransomware
For the hacker world there are no limits, even applications that are protected with encrypted or end-to-end encrypted files can be compromised. Ransomwares are programs capable of infiltrating documents, photos or any encrypted file with lower security or system weaknesses.
Once the ransomware enters, it can steal all information, visual, audio, files, chats, confidential data, banking and more. Therefore, the third party is at the mercy of the hacker and to recover it they must give it up monetarily and even then, there are no guarantees.
Hack Outlook with SQL Injection
SQLs are the most effective tools for detecting security holes in apps, platforms, web pages, devices and more. Using commands, hackers manage to infiltrate SQL injection, which is responsible for studying and monitoring the behavior of the third party within an app.
This in order to detect weaknesses in terms of passwords, security, confidential, public personal data and more. In this way, SQL injection manages to enter the app, acquiring all the information it wants, without the user realizing it and being able to do anything about it.
Hack Outlook with DNS Poisoning
Another method that is capable of manipulating, through advanced commands, information and people's access to other apps is DNS. By breaching DNS, the hacker has the power to redirect the victim to any malicious site they want and in this way the victim unknowingly logs into cloned sites.
A key example of malicious sites is fake logins, DNS allows the third party to not have to access any links. If not, you are redirected to a page identical to the official one and without noticing it, you enter your data, which is being collected in real time by the hacker.
Hack Outlook with Spoofing
A method that undoubtedly goes hand in hand with deception and the power of convincing is spoofing. This is characterized by violating accounts through deception and relying on other hacking methods such as hijacking, Trojans or viruses.
Its function is to impersonate support personnel or trustworthy entities on the website to request data, passwords, or confidential information. The person unaware of the deception ends up giving their information, which allows the hacker to take control of their platforms and more.
Hack with Outlook Hijacking
Hijacking is one of the complete takeover methods that abounds on the internet since it is not only dedicated to hacking as such. If not, it allows access to the victim's entire ecosystem of applications and devices remotely and in a few minutes.
How to protect your Outlook account?
Every Outlook account houses emails and confidential information about your activities and affiliations on the web. As well as important data from banking entities, for this reason it is essential that you always take these precautions to ensure your privacy and security on the Internet.
- 🔐 Periodically strengthen the security of your accounts, most platforms offer security monitoring to update and strengthen the security of your emails and data
- 🔐 Stay up to date with extra security news and two-step verification, this will help make it much more difficult to hack you
- 🔐 Find out about all the methods that exist to access your accounts anonymously and make sure you don't fall for them
- 🔐 Avoid disclosing information about your accounts, which could be used against you and benefit a hack.
- 🔐 Always open accounts from your devices, official platforms and avoid giving access to third parties.










