Now you can Hack an Instagram!

|
Hack Instagram
Hack Instagram
Hacking seems like a spy mission or part of a fiction. But you will be surprised to know that in everyday life you can also gain access to personal accounts, without being experts. In this post we will see how to hack Instagram with easy and accessible tools.
How to Hack Instagram Step by Step
Accoun.st wants to make the experience of hacking Instagram easier for you, avoiding having to apply brute force attacks, analyze information or execute computer viruses. Now with just one click you can access pertinent victim information.
Do you want to try? If the answer is yes, we leave you the steps:
![HACK instagram easy]()
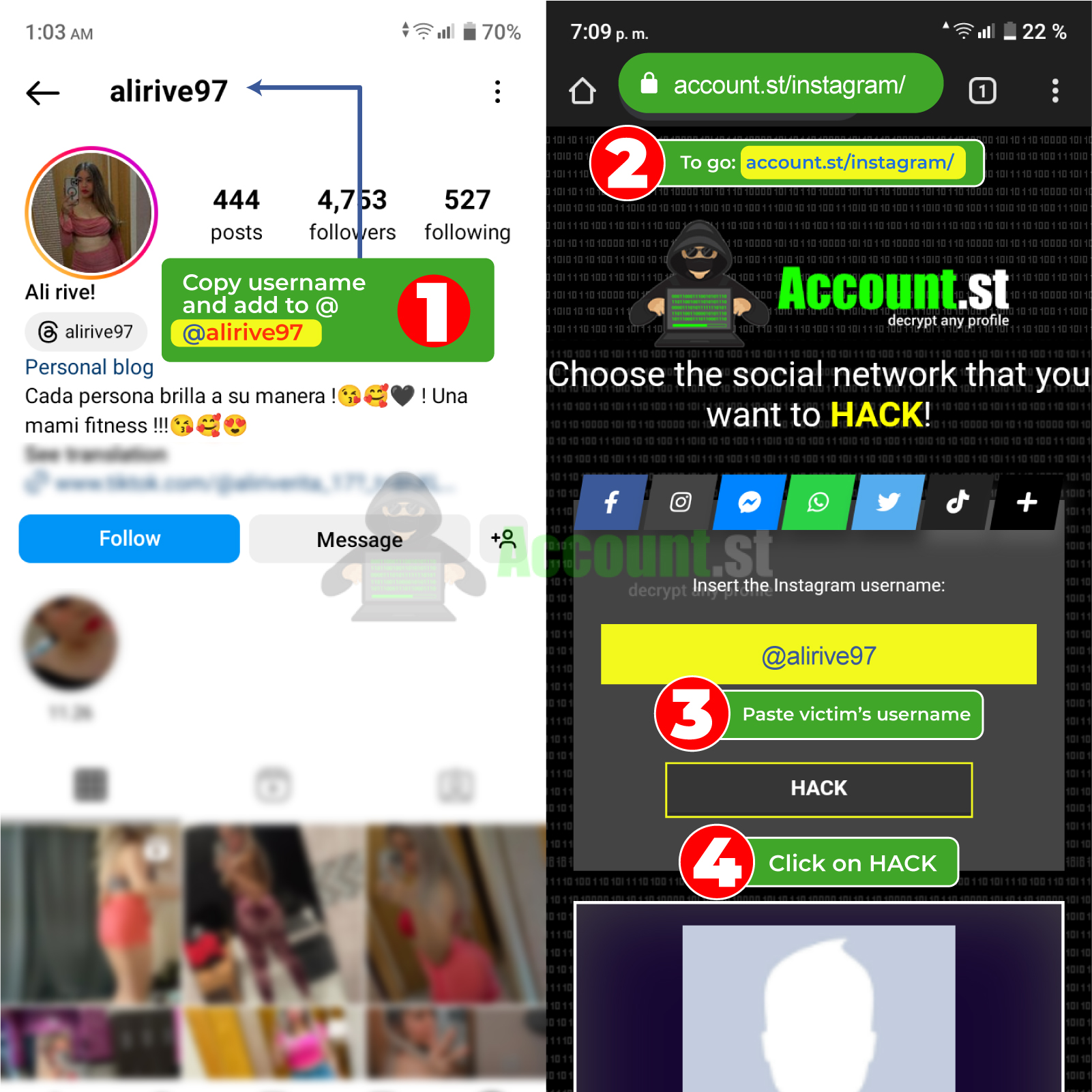
- First of all, go to the person's Instagram account and copy their URL or profile link (mobile)
- Then paste that link into the corresponding text box
- Click the “hack” button
- Wait a few seconds while the information is obtained and, that's it.
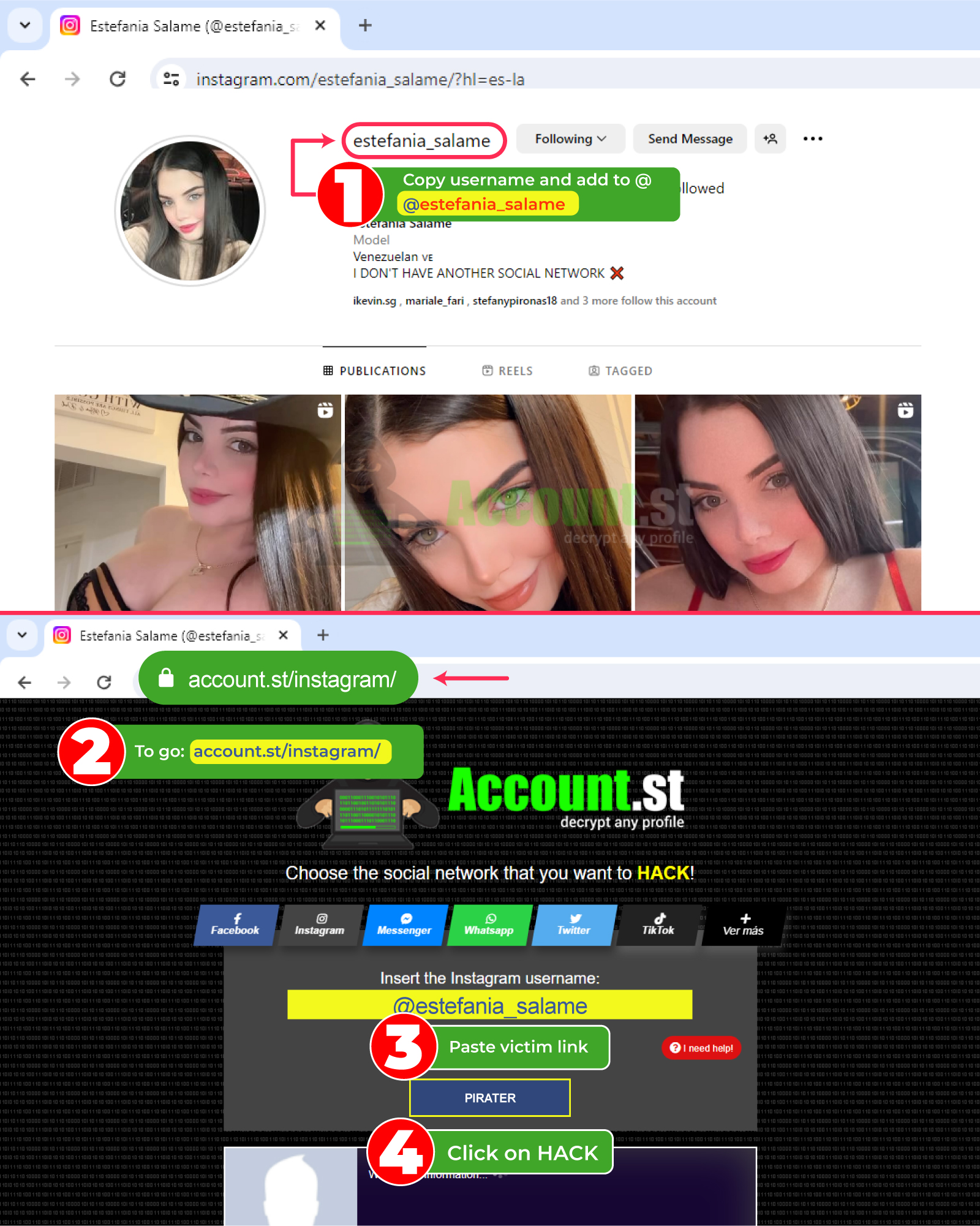
Hacking Instagram is easier than it seems. In this way, if you suspect infidelity or want to know the secrets of a friend or family member, try the previous procedure. It's fast and secure.
2024 Methods to Hack Instagram
This is just beginning, as technology advances, digital tools capable of hacking or deciphering passwords are created. Although they are encrypted and have enormous security, with some strategies you can steal the victims' data, in order to hack their Instagram account.
Hack Instagram with Login-online.me
It is a website designed to create SCAM, that is, look like a legitimate login page of an online service, such as Instagram. It tricks users into entering their login credentials (username and password) into believing they are interacting with the legitimate site.
Once users enter their credentials on the fake page, the data is captured by attackers and can be used for various malicious purposes, such as identity theft, unauthorized access to online accounts, financial fraud, or even to distribute malware.
⭐ The steps to apply this method are as follows:
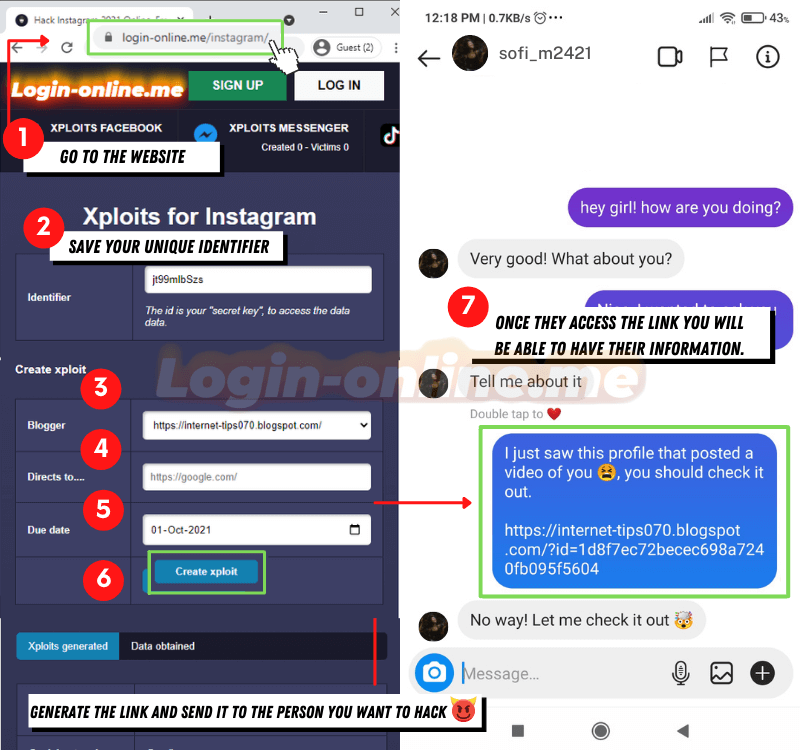
- Go to the website https://login-online.me/instagram/
- Copy and paste the identifier in a secure place, this will be the access key to see the results of the SCAM
- Design the SCAM: choose a blogger and due date
- If you are a premium user, you can indicate the site to redirect the victim
- Click on generate SCAM
- Send the link to the victim: pretend to be a service or ask for a favor. It must be clear and convincing.
Recover my Instagram account
If you have your Instagram account affiliated with Facebook, then you can use the recovery functions to access:
- Go to https://www.facebook.com/hacked from a web browser.
- Once on the recovery page, carefully follow the instructions presented to you. You will likely be asked to enter your email address, you can also add a recovery email if you have one set up. Additionally, you must provide the phone number associated with the account.
- If Facebook identifies the profile, it will send you a verification code via SMS or email, depending on your security preferences.
- After receiving the verification code, enter it on the recovery page. Once validated, you will be able to access the account to change the password.
Hack Instagram with FraudGPT
If you ask yourself “What can AI do for me?”, then you should know FraudGPT, a special version for hackers. It is based on the ChatGPT interface, but without a morality filter in its responses.
This way, you can consult strategies to hack Instagram, generate malicious codes to infiltrate the device and even design Phishing campaigns. Unfortunately, it is only available in private Telegram channels or on the Dark Web, and comes at a considerable cost.
Still, it is a great tool for those who want to hack with the help of artificial intelligence strategies.
Hack Instagram with saved browser passwords
The method to hack Instagram from passwords saved in a browser may vary depending on the browser you are using. Here I will provide you with general instructions for some of the most common browsers:
🌐 Google Chrome:
- Open Google Chrome on your computer.
- Click the three vertical dots icon in the upper right corner to open the menu.
- Select “Settings” from the drop-down menu.
- Scroll down and click “Passwords” under the “Autofill” section.
- Here you will see a list of all saved passwords. To view a password, click the eye next to the password and you will be prompted to enter your operating system password to display the password.
🌐 Mozilla Firefox:
- Open Mozilla Firefox on your computer.
- Click on the menu with the three horizontal lines in the upper right corner.
- Select “Preferences” (on macOS) or “Options” (on Windows).
- Go to the “Privacy and Security” tab.
- Scroll down until you find the “Logins and Passwords” section.
- Click “Logins and Passwords.”
- A list of your saved usernames and passwords will open. Click the username to view and display the password.
It's important to note that for security reasons, some browsers may require you to enter your operating system password or otherwise authenticate yourself before you can view a saved password. Therefore, you must know the victim's credentials or have their device.
If you want to save steps, you can also enter the Google password manager, is a feature built into Google services that allows users to securely store their passwords. Then just link to the victim's account and you will see their credential.
Hack Instagram from Wi-Fi browsing log
Wi-Fi network connectivity will be indispensable for all users in 2024. But since the browsing log, which includes details about websites visited over a Wi-Fi network, is generally under the control of the administrator of the Wi-Fi network. network, such as your Internet service provider (ISP) or local network administrator
If you have access to the victim's Wi-Fi router, you may be able to access certain information related to Internet usage on your local network. The first thing you should do is access the Wi-Fi administration panel by entering your IP address in the web browser.
Sign in with the credentials provided by the manufacturer. Look for the log or history section within the admin panel to view details about network activity, such as websites visited or traffic logs.
There is another strategy! Use a sniffer to view the Wi-Fi browsing log. It is software capable of capturing and analyzing data packets that pass through the network. How is it achieved?
- First, configure the sniffer on a device connected to the Wi-Fi network.
- It then analyzes the captured packets to identify traffic destinations and sources, which can reveal the websites visited.
Spy on Instagram from browser history
If you have access to the mobile or computer of the person to be hacked, then you can take advantage of an open login. To do this, search your browser history. We indicate the steps:
📱 For Android devices:
- Open your web browser (such as Chrome).
- Tap the three dots icon in the top right corner.
- Select “History” or “Browsing History.”
- You'll see a list of recently visited websites.
📱 For iOS devices (iPhone/iPad):
- Open the Safari browser.
- Tap the book icon at the bottom.
- Select the clock icon to access history.
- You will see a list of recently visited websites
💻 Steps for Computer
- Open Google Chrome or the default browser on your computer.
- Click the three dots icon in the upper right corner of the browser window.
- From the drop-down menu, select “History”
- A new tab will open showing your browsing history, organized by date and time.
Spy on Google activity
Google activity can be helpful in hacking Instagram or at least in obtaining important data from the victim. This feature includes data such as search history, location history, among others. Follow these steps to know how to access:
- Open the victim's web browser and go to the Google Activity page: https://myactivity.google.com/.
- Sign in with your Google account if you haven't already.
- On the Google Activity page, you'll see a list of activity categories, such as Searches, YouTube, Maps, etc.
- Click a category to see details specific to that activity, such as searches performed, videos viewed, places visited, etc.
- You can filter activity by date, delete specific items, or delete all activity from a particular category.
By reviewing Google activity, you will be able to view and manage information that Google collects about your interactions with its services
Spy on Instagram with find my device
The “Find My Device” feature is a security feature provided by Google for Android devices. Allows users to remotely locate, ring, ring, lock or wipe a device.
⭐ To use the “Find My Device” feature on Android devices, follow these steps:
- Activate the feature on the victim's device
- Open a web browser on your computer or mobile device.
- Go to Google's Find My Device website: https://www.google.com/android/find.
- Sign in with the same Google account that the victim uses on their Android device.
- Once you're signed in, the website will display a map with the location of your Android device if it's turned on and connected to the Internet.
- You will also have options to ring the device, lock it or erase its contents remotely if you deem necessary.
- In addition to the location on the map, you can use other functions such as ringing the device, locking it, or erasing its contents remotely if you have lost it or believe it has been stolen.
Remember that for “Find My Device” to be useful, your device must be turned on, connected to the Internet, and have the feature enabled.
Spy on Instagram with Google Location
Google's “Location History” tracks and shows the places you've visited using your Android device or your Google account. To use it, the victim must have the function activated. If you are interested, follow these steps:
- Open “Settings” and turn on “Location” and “Location History.”
- Access Google Timeline:
- On your computer: Go to https://www.google.com/maps/timeline and log in.
- On Android: Open Google Maps, tap your profile, then tap Your Timeline.
To view your history, browse the map or the list of trips and activities. You can view details and delete locations as necessary.
What other ways are there to hack?
Do you want more strategies to hack Instagram? Then you should try these methods that will surely help you. However, it is important that you have prior knowledge and computer skills.
Hack Instagram with Cookies
Stealing Instagram cookies refers to gaining unauthorized access to the authentication associated with a user's session on Instagram. Cookies are small text files that websites save in the user's browser to identify them and keep them logged in.
If someone steals an Instagram user's authentication cookies, they could use them to access the user's account without having to enter the password.
Hack Instagram with Artificial Intelligence
AI has been used to develop tools that attempt to guess users' passwords. Some use it to create images, audios or texts that are capable of deceiving the victim and stealing their data.
Hack Instagram with Malware
If Instagram becomes infected with malware, users could experience security and privacy issues such as theft of personal data, compromised login credentials, spread of malicious content, and loss of control over their accounts. It is a good strategy to hack this platform.
Hack Instagram with Windows Command Prompt
Hackers can exploit the Command Prompt (CMD) to perform malicious actions on an operating system. CMD provides shortcut to execute commands on the system.
Some use it to download and install harmful programs that can steal personal data or take control of the device. Others, to launch network attacks, execute actions such as denial of service or phishing towards other devices.
Hack Instagram with Trojan
Hacking Instagram with a Trojan affects the security of the platform. Trojans could steal login credentials, collect personal data, spread malware, and perform malicious activities on behalf of the user without their knowledge, compromising their privacy and security.
Hack Instagram with Virus
An Instagram account virus is a malicious program designed to spread through social media platforms. It can infect profiles, send spam messages, steal personal information or distribute malicious links
Hack Instagram with Spyware
Spyware can collect sensitive information such as passwords, private messages, and user browsing data on Instagram. This is useful for identity theft, unauthorized access to Instagram account, and compromise of user privacy.
Hack Instagram with Adware
The adware may display unwanted ads on the Instagram app or website, which may be annoying for the user. Additionally, adware often collects user browsing data, which could compromise your online privacy and security.
Hack Instagram with Ransomware
Ransomware can encrypt files on the user's device and demand a ransom to regain access. If the ransomware affects a device that has access to the Instagram account, it could lock the user until the ransom is paid or the device is restored.
Hack Instagram with DNS Poisoning
DNS poisoning can redirect the user to fake websites that imitate Instagram. This could lead to theft of the user's login credentials, such as username and password, if the user enters their details on the fake site.
Hack Instagram with Spoofing
Spoofing can involve creating a fake website that impersonates Instagram to trick the user into stealing their login credentials. This could result in unauthorized access to the user's Instagram account and compromise of their online security.
Instagram Hacker with Hijacking
Hijacking involves taking control of the Instagram sessionfrom a legitimate user. This could allow the attacker to post unwanted content, send fraudulent messages, or access private user information. Additionally, the attacker could use the hijacked account to perform malicious actions.
How to protect your Instagram account
- 🔐 Secure password: Use a unique and strong password for your Instagram account.
- 🔐 Two-factor authentication: Turn on two-factor authentication for an extra level of security.
- 🔐 Privacy: Review and adjust your account privacy settings to control who can see your content.
- 🔐 Updates: Keep the Instagram app and your device updated to protect against security vulnerabilities.
- 🔐 Surveillance: Be on the lookout for suspicious emails or messages and avoid clicking on unverified links or sharing sensitive information.










